While implementing security for Concordance is recommended but optional, security must be implemented when using Concordance with FYI Server. At a minimum you must enable security and require individual logons for each user, including administrators. Additional security measures include applying field and menu restrictions based off of user role templates that you create in the Concordance Security Console (File > Administration > Security).
Concordance security settings are enabled and respected by the FYI Server when users are imported into the FYI Admin Console as databases are registered. Any external authentication settings take precedence over Concordance database settings, adding an extra layer of security protection when accessing data through the FYI Server.
We recommend that you read this topic in its entirety to ensure you understand the nuances of setting up Concordance security for users accessing databases through the FYI Server, and have completed all necessary planning phases to ensure the security set up runs smoothly.
|
You can also layer security in the FYI Admin Console by adding database and server firewalls. For more information about server firewalls, see About setting up and managing firewalls. For more information about database firewalls, see Adding database firewalls. |
We recommend that before you set up users and apply security permissions, that you pre-plan the following items noted in the Setting Up Security Checklist.
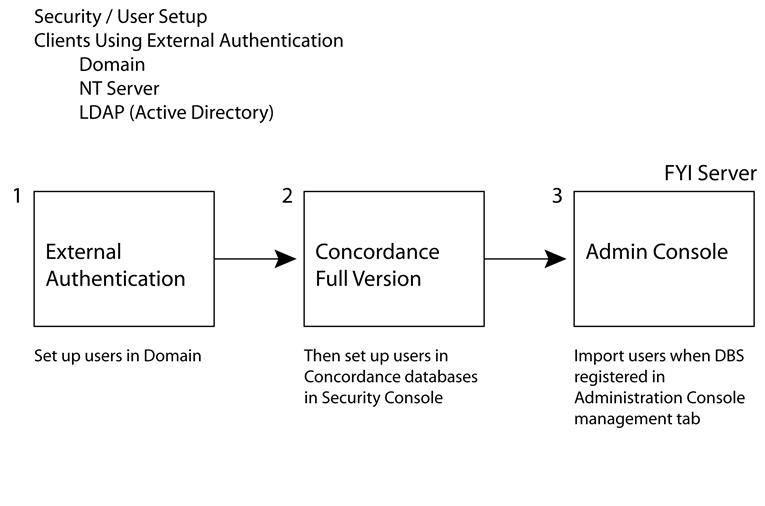
•If you are using external authentication, you want to set up your users first in the Microsoft Active Directory and add them as users to Concordance databases, and then import the users into the Administration Console when registering databases.
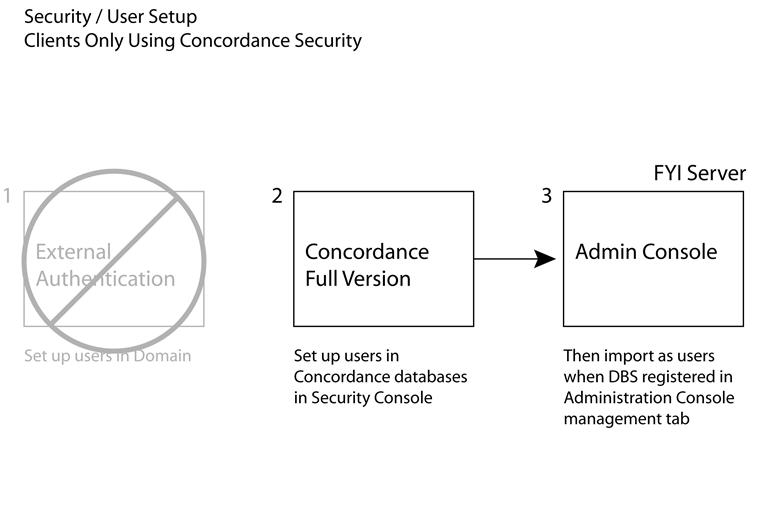
•If you are not using authentication, we recommend that you set up users in Concordance databases first and import the users into the FYI Admin Console when registering databases.
Checklist: Setting Up Security
Pre-Planning for Security |
|
|---|---|
|
Have you determined if external authentication will be implemented in addition to Concordance security? |
|
Do you have a method of assigning and tracking user IDs and passwords to help manage individual user accounts for access to Concordance, FYI Reviewer, and the FYI Server? |
|
Have you planned and designed user roles with pre-defined security settings based on the types of administrators and users that are accessing databases? |
|
After you set up user role templates, have you determined whether you will remove the default user account? |
|
Have you implemented a process for setting up security, adding users to databases and the FYI Admin Console, and how you will manage adding new users for Concordance .FYI and FYI Reviewer after databases are published? Are these processes known to other administrators who are responsible for setting up users and managing databases? |
|
Did you implement a folder template to store your databases and associated files? |
Concordance Security |
|
|
Did you set the administrator credentials for the applicable databases in the Security dialog box in Concordance, and did you give them full access to all fields and menu items? |
|
Did you import additional administrator accounts from a .csv file for your organization and set full menu and field access rights? (Optional) |
|
Have you created user role templates in Concordance databases on which to base user accounts and access for pre-defined settings, such as attorney and paralegal, or administrator and reviewer? Note: User role templates help save time when adding new users and reduce security risks if you have pre-defined field and menu access already designated in the templates. |
|
When you set up individual user accounts for users in Concordance databases, did you remember to enable security and require logons? |
|
Did you verify field rights and menu access as designed in user templates and customized per user, as needed? |
|
Did you export a backup copy of the .csv file for reference, and save it to a specified location in the folder template? Note: You can import the .csv file into other Concordance databases to save time with user set up. |
FYI Admin Console Security |
|
|
Have you added additional administrators to the FYI Admin Console on the Administration tab? Did you set up e-mail options and watchdog services for each additional administrator? |
|
Did you register the database in the FYI Admin Console and verify that all user accounts imported as specified during set up? |
|
Did you specify a database administrator per individual database on the Management tab > Databases side tab > Administration side tab? |
|
Have you considered whether public databases should be shown or hidden? |
|
Did you associate your Concordance databases to the client and matter that applies for each database? Note: FYI Reviewer users cannot access databases unless they are associated with a matter. Clients are for organizational purposes only. |
|
Did you add additional contact information for each user on the Management tab in the event that the user or main contact for a case needs to be contacted? |
|
Did you distribute .fyi files and the FYI Reviewer URL to users? |
Security Options
When using FYI Server, you have two primary security options:
•External - FYI Server relies on an external source to validate users.
•Internal - Concordance determines whether a user has access to a database or to view matters.
Using External Authentication
When using Concordance with Microsoft Active Directory, Microsoft Windows NT or PDC (Primary Domain Controller) to authenticate users, a two-fold verification takes place. The user is first authenticated with one of the following: Active Directory, Windows NT or PDC. If the person is a valid user, they are then authenticated in the Concordance Security Console and will have permissions based on the security rights applied.
To use this method of user verification, the login IDs in Concordance must be identical to the login IDs used in the directory service on the network. Also, ensure that passwords are set to never expire.
To add outside users to the FYI Server when using this type of authentication, the user must be added to the directory service on the network as well as in the Concordance Security Console (File > Administration > Security). For security purposes, they can be assigned no rights at the network level – but they need to be listed in the network directory for the authentication to take place. In the Concordance Security Console, users can be added and granted the appropriate rights they need for the case. The same rules apply with regard to matching logons in both the Active Directory and Concordance Security Console.
For more information about authentication types, see Setting authentication types.
Authentication Type Considerations
FYI Server supports a variety of authenticators that determine what source grants or denies users from accessing resources and the hosted databases. Please read the following sections before you adjust settings for authentication types.
Supported Authentication Types
Internal Types |
Description |
|---|---|
Concordance |
Concordance handles authentication. A valid user ID and password is required to connect. |
External Types |
Description |
External by Domain |
Authentication by NT Domain Controller (non-Active Directory) |
External by NT Server |
Authentication by stand-alone server (Member server) |
External by Active Directory LDAP |
Authentication by Lightweight Directory Access Protocol (Microsoft Active Directory) |
|
If you are using external authentication, you must still use Concordance security. |
Concordance
This authentication method verifies user credentials set in the Concordance Security Console. Concordance will give users their designated field and menu access. Users who are not verified by the Concordance settings are refused access by the FYI Server.
External by Domain
Domain passwords take precedence over Concordance passwords:
•If a user name or password is not recognized by the domain controller, then the user is refused access by the FYI Server.
•If the user is verified by the domain controller, then the user is given access to all Concordance databases where Concordance rights allow access for that logon, regardless of the Concordance password.
The External by Domain setting typically requires use of several ports: 137 TCP, 138 UDP, 139 TCP, and 445 TCP. Please ensure that your firewall is not blocking these ports.
|
If you’re using FYI Server 2.0+, you can verify user credentials through your Windows NT Primary Domain Controller (PDC) or Backup Domain Controller (BDC). |
External by NT Server
This authentication method verifies user credentials through your Windows NT Primary Domain Controller (PDC) or Backup Domain Controller (BDC), specified by the Internet or IP address. This method has the same restrictions and features as described above for the External by Domain method.
If you enter an IP address and the server's IP address changes, FYI Server will not be able to communicate with the credential server until the address is manually updated.
Port addresses typically required by this method include 137 TCP, 138 UDP, 139 TCP, and 445 TCP. Please ensure that your firewall is not blocking these ports.
External by Active Directory
Microsoft Active Directory passwords take precedence over Concordance passwords.
This authentication method requires a Microsoft Active Directory compatible credentials server. User credentials are verified and used as described above for the External by Domain method.
If you enter an IP address and the server's IP address changes, FYI Server will not be able to communicate with the credential server until the address is manually updated.
Firewall ports that need to be open for Active Directory include 389 (LDAP), 636 (secure LDAP), and NetBIOS ports for the change password feature.
|
When authenticating users against an Active Directory server in a domain other than where FYI Sever is located, make sure that the FYI Server is running on Windows Server 2016. |
For more information about setting up users in Active Directory, see Setting up users in Active Directory.