A firewall is a piece of hardware or software that can prevent unauthorized access to or from a private network. Firewalls can be added for the FYI Server and the FYI Administration Console Server from the Firewall tab in the FYI Admin Console. You can also add firewalls to databases when you are registering them on the Management tab.
For more information about adding database firewalls, see Adding database firewalls.
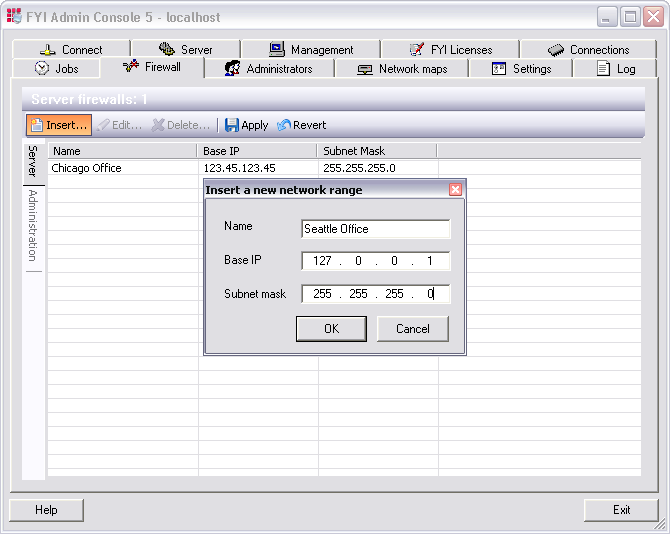
Server firewalls are an optional but powerful security feature and are used to augment user access settings and maintain security when exposing the FYI Administration Console Server to public IP ranges. Using firewalls determines the IP ranges that are allowed access to the FYI Administration Console Server.
Access to servers is provided only to clients and users connecting with a network address listed in the Firewall list on the Firewall tab. Clients and users using other addresses are blocked. We highly recommend that you implement server firewalls to protect databases from unwanted access, especially if the FYI Server is installed on the DMZ (demilitarized zone).
|
By default, firewalls are not enabled and the servers will accept connections from anywhere. Once a firewall is added, only the connections listed on the Firewall tab are allowed. |
The FYI Admin Console is protected by password access, even when the firewall option is not used. Administrators can log on to the FYI Admin Console using an administrator user name and password.
The FYI Server provides access to databases and subsequently affects all databases. Databases can be accessed remotely with Concordance using valid .fyi database files. Users can also log on to FYI Reviewer with a valid user name and password. Access to published databases in FYI Reviewer is protected by database security settings. Firewalls are not required for databases registered in the FYI Server, but can be used to limit the IP range used to access databases.
|
Database firewall settings take precedence over server firewall settings. |
FYI Server Firewall Overview:
•Can be configured to limit connections to certain sources
•Defaults to allow credentialed users to connect from any source
•No connections sources are blocked until you create first authorized connection source
•Must use subnet accounts only
•Can adjust settings to work with existing firewalls
•Managing firewall settings is a common troubleshooting issue
•Database-level firewall overrides FYI Server firewall settings
|
Remote access needs require additional planning. Remote users working from a hotel, court room, home, etc. need to have exceptions set in order to access databases through the firewall. |
|
If you are using VMware, you may run into instances where you receive multiple MAC addresses. FYI Licenses are assigned to one specific MAC address that is automatically pulled from the NIC (network interface card) that was physically connected when the licenses were registered. If you run into a situation where you need to update the MAC address, contact Concordance Technical Support. |