Encryption and TLS Protocols
As of version 7.3, LAW supports TLS 1.2 encryption protocols for Windows 10 systems.
•For information on enabling TLS on your environment systems, we recommend you work with your Administrator.
•LAW is compatible with systems running TLS 1.2 encryption; TLS 1.0 may be disabled on these systems.
•For instructions on enabling/disabling TLS 1.2 and 1.0, please reference https://docs.microsoft.com/en-us/windows-server/security/tls/tls-registry-settings.
LAW FIPS Compliance and Configuration
Effective starting with version 7.5.X, CloudNine LAW is certified for FIPS encrypted Windows 10 operating systems.
Administrators can enable FIPS via either local system registry; or Group Policy.
When enabled, the operating system will ensure that only FIPS validated hashing and encryption modules are used by the operating system (including .NET libraries).
For more information on the FIPS encryption and usage with Windows 10, the STIG guidelines are listed here for reference: https://www.stigviewer.com/stig/windows_10/.
Users can also reference the STIG guidelines for enabling FiPS encryption: https://www.stigviewer.com/stig/windows_10/2019-01-04/finding/V-63811.
Antivirus Best Practices and Recommendations
With any eDiscovery processing tool, an anti-virus scanning utility can alter files and interrupt chain of custody and hashing values.
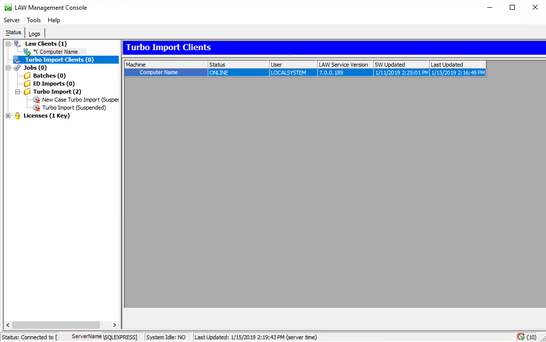
Opening/Closing the LAW Management Console
To open the LAW Management Console, locate and run LAWConsole.exe from your LAW install directory, usually found in C:\Program Files (x86)\LAW50\Console\.
1.Use Windows Explorer to browse to the path that contains the LMC executable file. By default, file path is:
C:\Program Files (x86)\Law50\Console\
2.Double click LAWConsole.exe.
The LAW Management Console screen appears.
3.The LMC is configured through the LAW Configuration Utility. It will use the same SQL server that is configured as the Management Database.
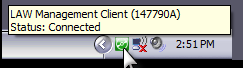
Once opened, the LMC will continue to run in the background, even if the window itself is closed. To re-open or fully close the LMC, use the LAW Management Client icon in your system tray.
![]() To Open LMC
To Open LMC
 Windows 10/Windows Server
1.Mouse over the LMC icon located in the Windows notification area. 2.Click the LMC icon or right click the icon and then click Restore. The LMC starts. •If necessary, log on to an instance of SQL Server. •If the LMC icon is not visible in the Windows notification area, see the previous section in this topic To start the LMC for the first time.
|
![]() LMC in the Notification Area
LMC in the Notification Area
You can use the LMC icon in the Windows notification area to restore the LMC, stop the LMC, or perform a quick check of its connection status to SQL Server.  Windows 10/Windows Server
1.Mouse over the LMC icon located in the Windows notification area. 2.Perform the following tasks as needed:
|
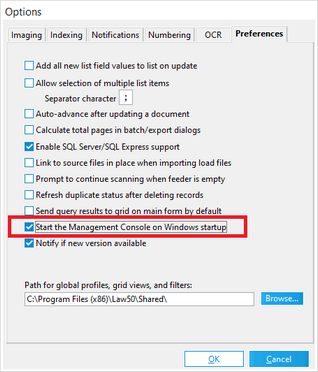
![]() To Configure LMC to Start with Windows
To Configure LMC to Start with Windows
|
1.Start CloudNine™ LAW. 2.From the main window, on the Tools menu, click Options, and then click Preferences. 3.Select the Start the Management Console on Windows Startup check box. 4.Click OK. Click Yes if you are prompted to start the LMC. The LMC starts. Every time you restart Windows, the LMC will also start automatically but run minimized. You can then restore the LMC by selecting its icon in the Windows notification area.
|
Best Practices for insulating against unwanted AV impacts in processing include:
•Separate the Processing Network and other Review and Business Networks (e.g., separate LAN or vLAN).
•Only run virus scanning after processing is completed (e.g., when moving processing volumes to new locations for Production or Review Loading).
•If on-demand virus scanning is a compliance requirement, then scan only the file shares with extracted ESI.
•These paths should be excluded to avoid impacts to processing speed and reliability:
oInstallation directory
oLocal User Log Directory
oLocal User Data store Directory
oLocal Computer Data store Directory
oLAW Case Directory
oLAW Worker Temp Directory
oSource data location
Additionally, users may reference the EDRM recommended practices regarding virus protection here: https://www.edrm.net/resources/frameworks-and-standards/edrm-model/edrm-stages-standards/edrm-processing-standards-guide-version-2/.
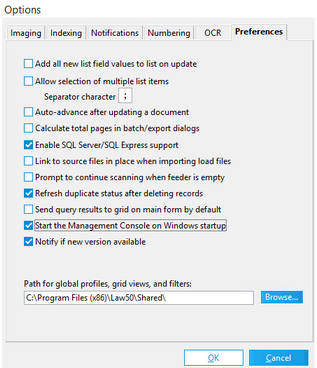 Set up your LAW case preferences
Set up your LAW case preferences
Tools > Options..., navigating to the Preferences tab within the Options window
It is highly suggested to turn on
•"Refresh duplicate status after deleting records"
•"Start the Management Console on Windows startup"