The FYI Server uses a variety of security methods to ensure data integrity, security, and high performance. Please read this section carefully, prior to implementing security for the FYI Server, Concordance, and FYI Reviewer.
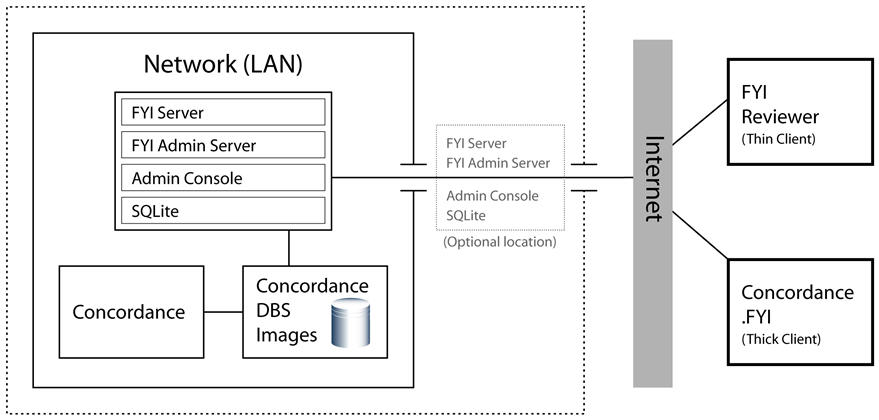
FYI Server Connections
Concordance and FYI Reviewer connect to the FYI Server using an TLS 1.2 encrypted connection. This connection is fully compatible with firewalls that monitor and verify TLS 1.2 traffic. Unlike a standard Web server connection, the FYI Server connection is kept open for the entire session for both efficiency and functionality. The connection is kept open to send progress messages, to update interactive search results and progress meters, and to perform other operations that would not be possible with repeated and unnecessary connections and disconnections.
Encryption
Data passed between the FYI Server and clients is both compressed and TLS 1.2 encrypted for high speed and security. Concordance uses both RSA public and private key encryption. All data is transmitted using RSA 128-bit encryption. The initial handshake conversation is encrypted using 1024 bits. This is the same TLS 1.2 encryption used by web servers for tasks such as online banking. We recommend that you install the server on TLS 1.2 Port 443, as it is fully TLS 1.2 compliant.
Firewalls and Ports
The FYI Server can use its own firewall. This is available in addition to your organization’s own firewall. The FYI Server firewall can be configured to allow only specific IP addresses or address ranges for a single database or for the entire server. While firewalls are not required, access to published databases is protected by database security settings and optional database firewalls.
The FYI Administration Console Server is protected by password access, even when the firewall option is not used.
Administrators can log on to the FYI Administration Console Server using an administrator user name and password. Firewalls are not required, but can be used to maintain security when exposing the FYI Administration Console Server to public IP ranges. Using firewalls determines which IP ranges are allowed access to the FYI Administration Console Server.
Setting Port Addresses:
•End-user traffic for FYI Reviewer or .fyi files via the FYI Server – Default Port is 443
•Administration traffic via the FYI Admin Server – Default Port is 10001
|
We recommend that you periodically check your ports to ensure they are open to inbound/outbound traffic. |
For more information about modifying port addresses, see Adjusting port settings.
For more information about setting database firewalls, see About setting up and managing firewalls.
DMZ or LAN?
The FYI Server can reside on your LAN or in your DMZ as your data security policy dictates.
•If you are using external authentication, you can install the FYI Server on the DMZ in addition to applying Concordance security and setting up domain users. User logons and passwords must be identical in both security locations in order for reviewers to access databases in the FYI Server.
•If you are only applying Concordance security, we recommend that you install FYI Server on your LAN because the DMZ generally requires opening a connection from the server to the LAN, which can create a security risk.
We also recommend using NAT (Network Address Translation) to open an inbound port to the server and installing the server on TLS 1.2 Port 443, as it is fully TLS 1.2 compliant.
Authentication Types
Microsoft Windows NT, Microsoft Active Directory, and PDC secure login can be used by the FYI Server, making user administration easy and fully integrated with your existing network policies. FYI Server will use NT, PDC, and Active Directory authentication, passing all login and passwords to your existing domain server for verification and enforcement of password policies including expiration, length, mix of alphanumerics, and all other policy restrictions used by your organization.
FYI Server with Active Directory, Windows NT, or PDC can be used to verify users’ credentials. Logins are checked with Windows Security Controller. Setting this up helps ensure conformation with password policies.
Supported Authentication Types |
|
|---|---|
Internal Types |
Description |
Concordance |
Uses the .sec file to authenticate users. Highly recommend always implementing a user login and password to connect. |
External Types |
Description |
External by Domain |
Allows for authentication against an NT Domain Controller (without Active Directory). |
External by NT Server |
Allows for authentication against a stand-alone server (Member server). |
External by Active Directory LDAP |
Uses the Microsoft Windows Active Directory to authenticate users (Windows 2003 and above). Authentication by Lightweight Directory Access Protocol (Active Directory). |
For more information about external authentication and how it relates to user security, see About setting up user security.
Using Microsoft Active Directory
If you are using external authentication, you will need to first set up users in Active Directory and then add the user's name in the Security Console of the Concordance database, before specifying Concordance .FYI or FYI Reviewer users in the FYI Admin Console. When using external authentication, it is important that user names match in both the Active Directory and the Concordance database.
We also recommend registering databases in the FYI Admin Console as a means of adding users to the FYI Server. User accounts are enabled in the FYI Admin Console on the Management tab .
For more information about setting up users in the Active Directory and Concordance, see Setting up users in Active Directory.
File Storage Considerations
File size and storage considerations are additional planning elements when setting up the FYI Server.
You need to ensure the following:
•The server hosting FYI Server can access other servers easily
•That FYI Server can access files easily
•Databases and images are local to the server
•There are not any latency issues arising from databases or image files that are too big
You can choose to store databases and images in two ways:
•LAN For this setup, we recommend you store databases and images on the same server as the FYI Server to reduce any latency issues in accessing files.
•Network Accessible Storage You can choose to store databases on one network device and images on another, and have the FYI Server point to these locations to access them. Latency differentiations are minor if database size is kept smaller and all images are processed as single TIFs.